Manage Threats & Configuration Weaknesses to minimize your attack surface
Vulnerability Management
Vulnerability Management
Associate threats with vulnerabilities to orchestrate and automate response actions
What is Vulnerability Management
Manage, classify, prioritize, assign, and monitor the process of remediating vulnerabilities and configuration weaknesses to minimize your attack surface. Associate vulnerabilities and configuration weakness with threats targeting your organization to prioritize your actions and minimize the impact of a materialized threat.
The Challenge
Why you need Vulnerability Management
Managing and monitoring the remediation process of identified vulnerabilities and configuration weaknesses can drain your valuable time and resources while distracting you from real threats where your attention is truly needed.
Intelligently minimizing false-positive security alerts is a key component of minimizing your attack surface and exposure to targeted threats.
What’s Under the Hood
How it works
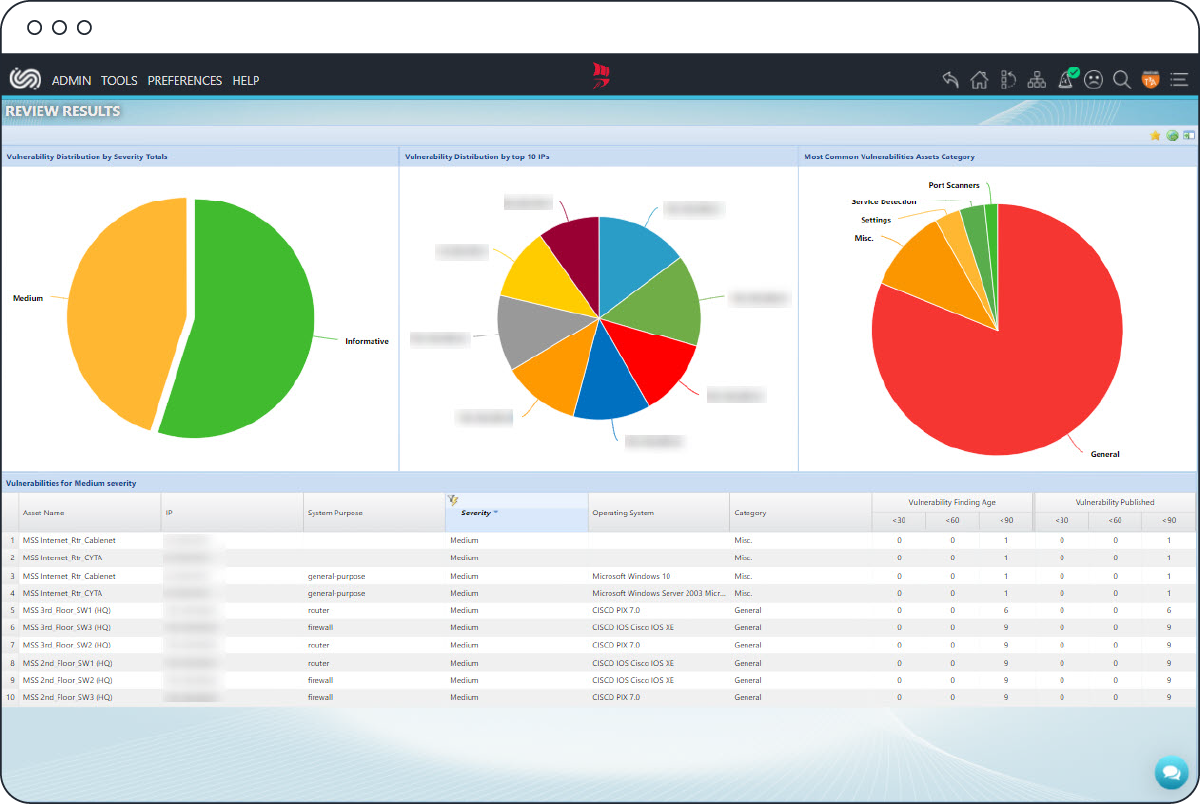
ClearSkies™ Vulnerability Management imports scan results from various third-party vulnerability tools. It simplifies the monitoring and management of the remediation process of vulnerabilities and configuration weaknesses towards minimizing your attack surface.
User-uploaded scan results assist in the pre-correlation process, providing a multi-dimensional assessment of the impact of an incident.
Furthermore, it associates identified vulnerabilities and configuration weakness with threats targeting your network, systems and applications, enabling you to prioritize your mitigation actions, and at the same time, minimize false-positive alerts by up to 95%.
This way, your security staff can quickly resolve benign alerts, granting you the time and valuable insight to focus on actual threats.
Benefits
What you get
Assess, prioritize, act and manage the outcome of a vulnerability assessment exercise.
Prioritize vulnerabilities based on their classification and impact.
Associate threats with corresponding vulnerabilities as they emerge to orchestrate and automate response actions.
Drastically reduce false-positive alerts (up to 95% reduction), saving valuable time and resources that would otherwise be diverted from focusing on actual threats.
Ecosystem
How does Vulnerability Management tie into the ClearSkies™ Threat & Vulnerability Management Platform?
Vulnerability Management is part of the cross-layered extended detection and response capabilities that enable you to associate threats with vulnerabilities while automating and orchestrating response actions.
Learn more about the ClearSkies™ Threat & Vulnerability Management Platform ecosystem.
Intuitive User Experience
Secure Web Portal (SWP)
Real-time visibility of your security posture made easy.
Mobile App
Real-time visibility while on the go.
Demo request
See it in action!
Request a live demo from our representatives to experience the value of ClearSkies™.