- Why ClearSkies™
- Products
Platform Overview
ClearSkies™ Threat Detection, Investigation & Response (TDIR) platform takes a risk-based approach to help organizations minimize Attackers’
Dwell-Time, simplify the investigation process, prioritize response actions thus optimizing SOC operations.SIEM
Real-time visibility over your network through Advanced Security Analytics, either on-premises or in the cloud.
Add-onsEndpoint Detection & Response
Enhance your threat detection and early response capabilities.
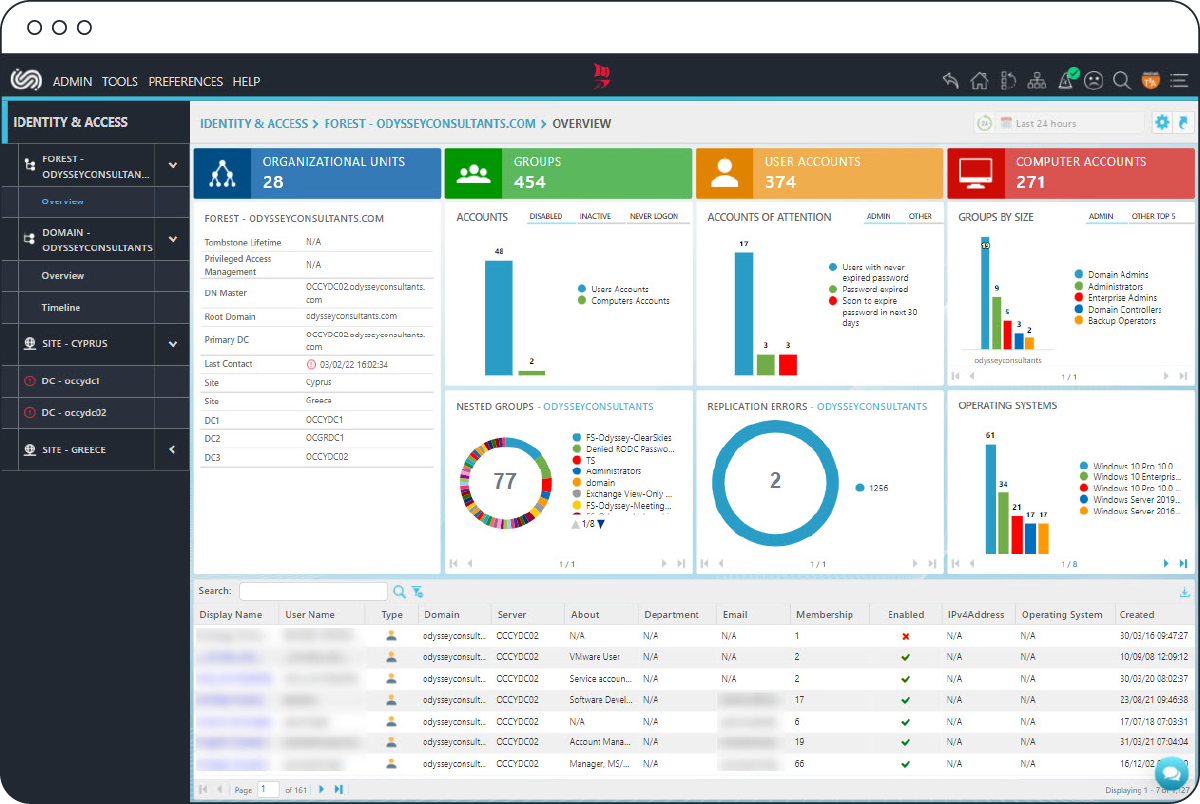
Identity & Access
Stay on top of your user base.
Active Defense
Lure, trap, delay and unmask threat-actors.
Vulnerability Management
Focus on real threats by reducing false positives.
Marketplace
Extend the power of your SIEM.
Service Delivery
Considering the varying sizes, needs, complexity, internal capabilities, budget constraints and cybersecurity management maturity levels of different organizations, ClearSkies™ SIEM is a flexible and scalable service delivery model offered as follows: ClearSkies™ SIEM, MS/MDR and Hybrid.
- Services
- Solutions
- MSSP’s Platform
- Resources