SIEM
recognize patterns of suspicious behavior
Unlock the Intelligence of your Data
What is ClearSkies™ SIEM
An award-winning modern SIEM deployed via the innovative data-forwarding appliance ClearSkies™ iCollector™. ClearSkies™ SIEM is implemented on premises, in the cloud or in a hybrid environment. Manage it on the ClearSkies™ Secure Web Portal (SWP) centralized console, or while on the go with the ClearSkies™ Mobile App.
What it does
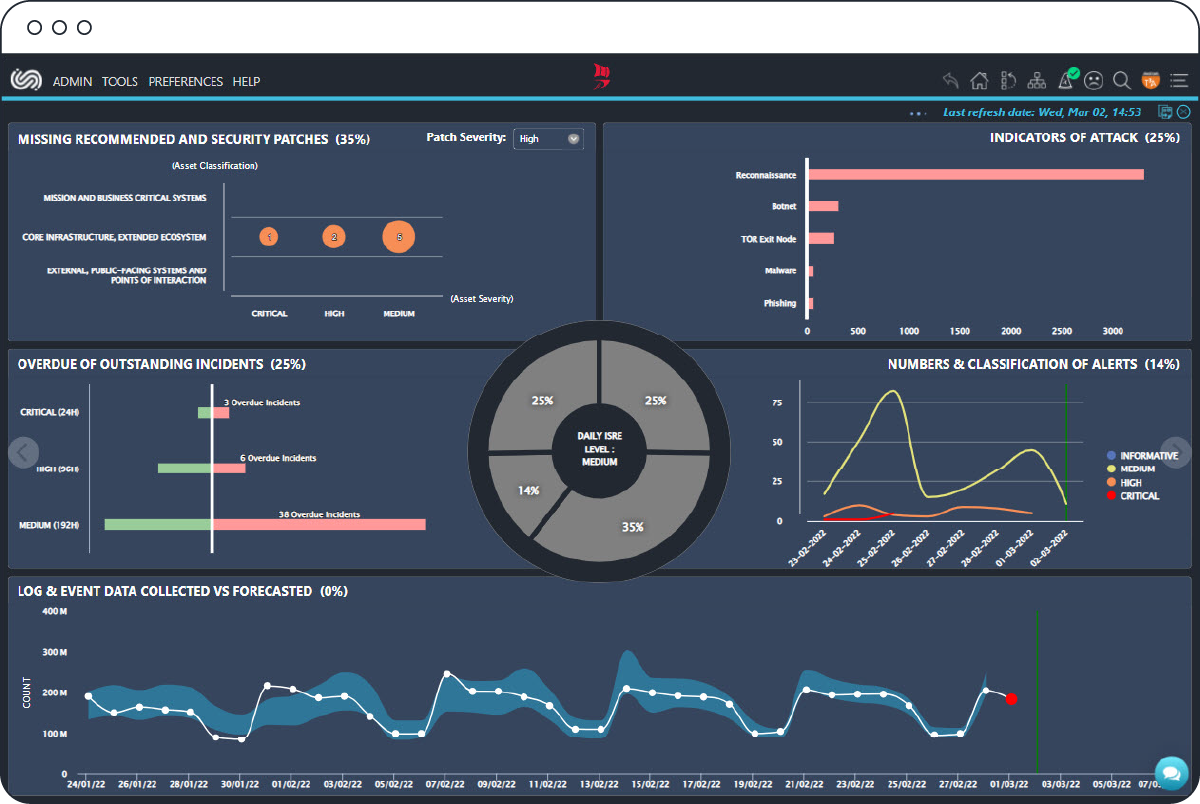
It provides real-time in-depth Intelligent Analysis and Correlation of log and event data collected from heterogeneous data sources combined with evidence-based knowledge of emerging threats and vulnerabilities to produce actionable information.
What you get
The outcome of this process assists Information Security, Network & Digital Assets, and Compliance & Risk Management operations and Risk Management personnel to respond to threats, assess incidents, reduce downtime, conduct forensic investigations, assess the level of risk, and prepare relevant audit and compliance reports.
What’s under the hood
Advanced Machine Learning (ML) and Artificial Intelligence (AI), including User & Entity and Behavioral algorithms give you the power for the early detection of and response to advanced malicious cyberattacks and suspicious user activities with the use of Security Orchestration & Automation.
ClearSkies™ SIEM utilizes Machine Learning (ML) and Artificial Intelligence (AI) algorithms to drastically improve the detection and forecasting capabilities pertaining to suspicious/malicious and 0-day cyber-threats, including users’ abnormal activity/behavior, which would otherwise go unnoticed/undetected by conventional SIEM technologies.
Extract Value from your Data
These unique advanced analytic capabilities empower your organization to assess how datasets behave over a time period, this way extracting usable and actionable information out of vast volumes of seemingly meaningless data.
Minimize Your Detection Deficit
Streamlining your Threat & Vulnerability Management Process
ClearSkies™ SIEM streamlines your Threat & Vulnerability Management Process by significantly accelerating your proactive threat detection and response capabilities, thus drastically reducing your “Detection Deficit” (time between breach and discovery). At the same time, it safeguards the Confidentiality, Integrity and Availability of sensitive information found within your log and event data.
Safeguarding Confidentiality
Modular Deployment
Customize and expand your SIEM’s capabilities
ClearSkies™ SIEM expands with over-and-above add-ons and third-party integrations for optimal visibility and effectiveness, according to your specific needs and operational maturity levels.
Intuitive User Experience
Secure Web Portal (SWP)
Real-time visibility of your security posture made easy.
Mobile App
Real-time visibility while on the go.
Try ClearSkies™ SIEM on your organizational network and get real actionable results now!

Servicemodules
Discover the ClearSkies™ out-of-the-box functionality
Explore one by one the different ways by which you gain value through specialized ServiceModules, from incident investigation and automated response to compliance status monitoring and internal audit.
Learn More
Get the ClearSkies™ Centric AI Brochure
Your data have a story to tell. Discover patterns of suspicious/malicious behavior hidden inside your network activity.