Overview
Why you need UEBA
The information-threat landscape is evolving. The volume, velocity, complexity and sophistication of attacks are consistently becoming more advanced, and they very often bypass conventional/traditional security defenses.
UEBA focuses on detecting insider threats, such as compromised employees, or employees who may attempt to steal sensitive data, perform fraudulent attempts and carry out targeted attacks.
How it works
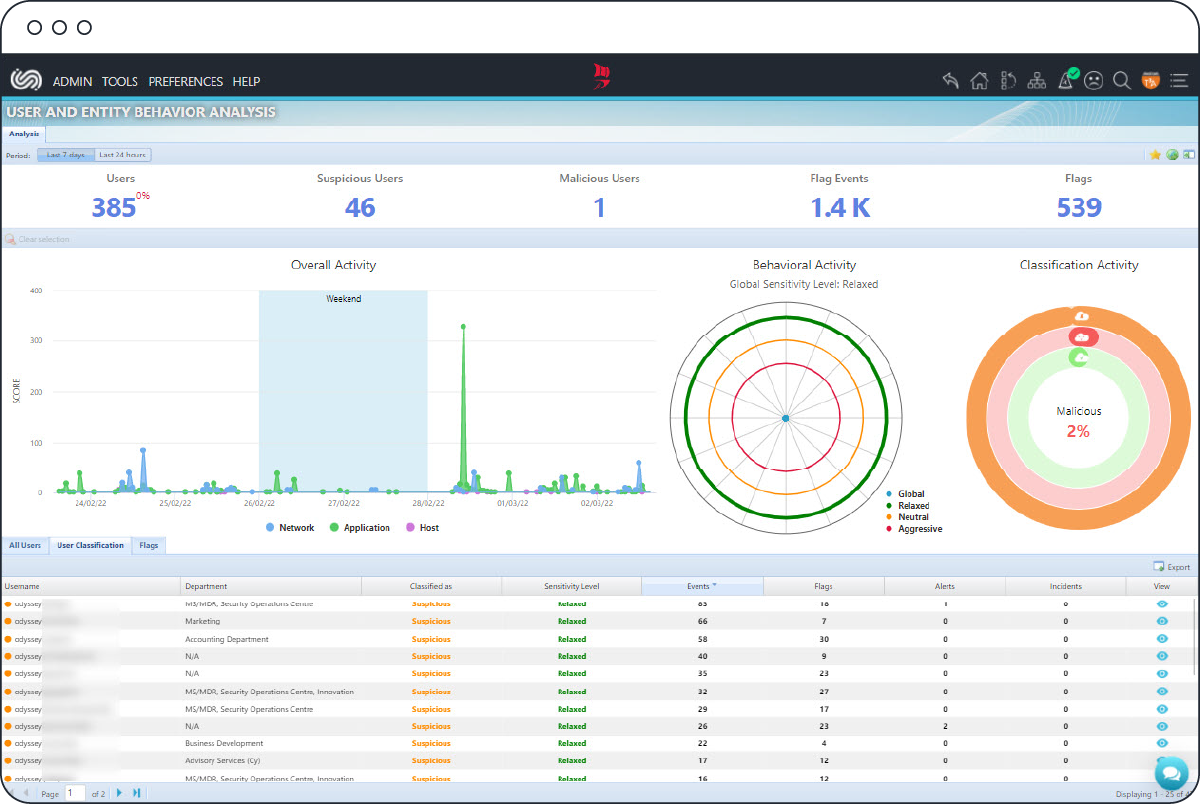
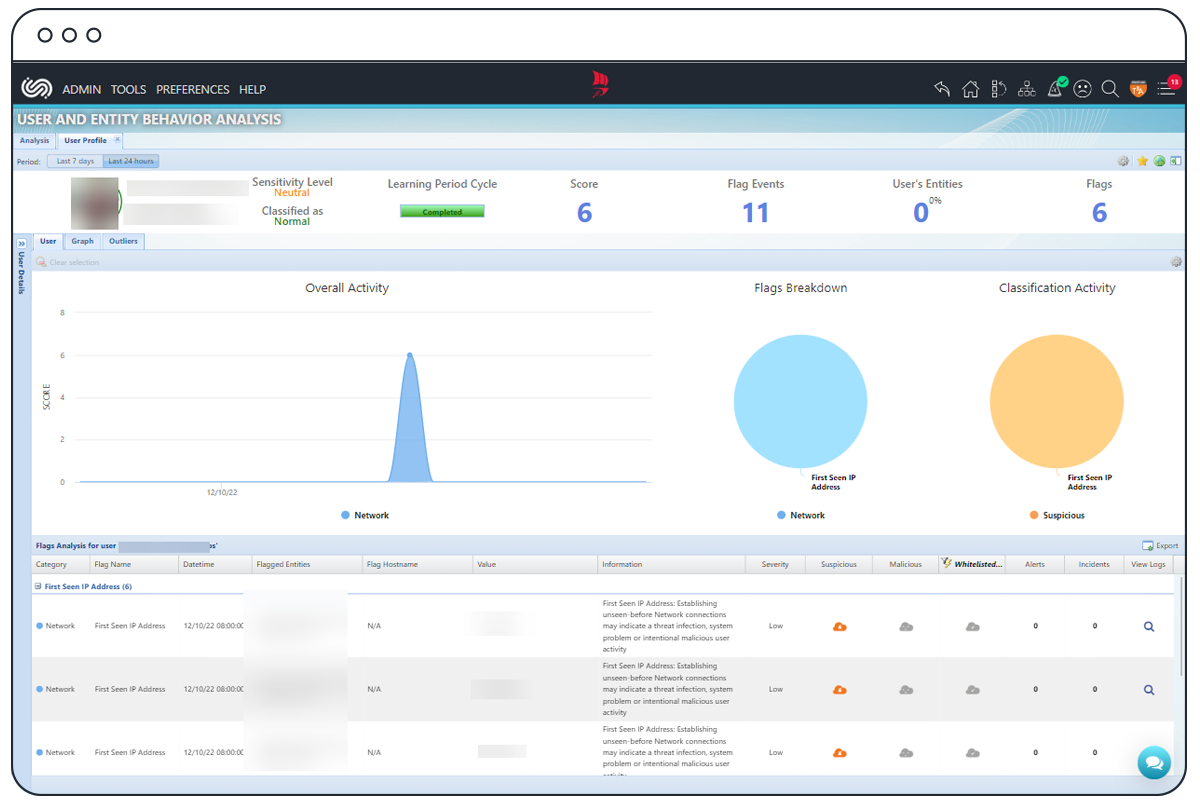
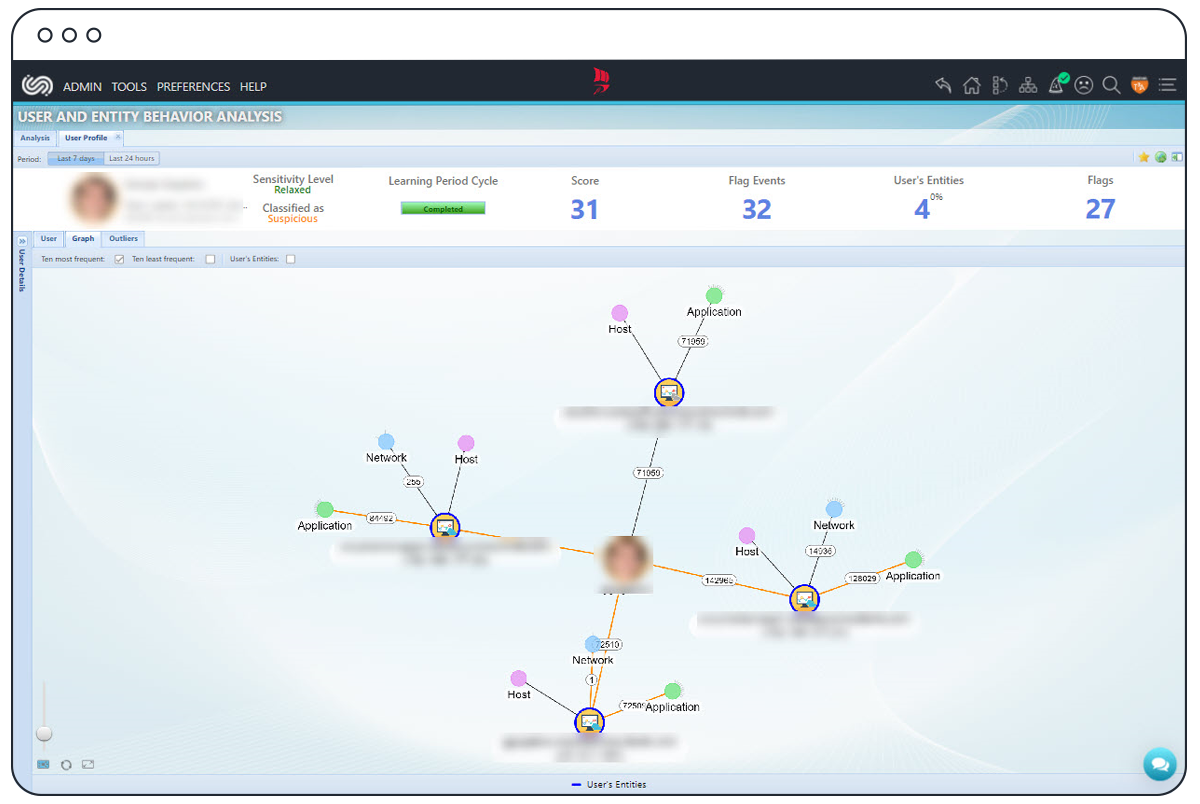
UEBA is the process of profiling/baselining user-related host/network/application activities for detecting suspicious/malicious behavior and intrusions by identifying meaningful anomalies or deviations from “normal” patterns of behavior.
This feature is state of the art, and constitutes the gold-standard contemporary approach to unearthing elusive and potentially catastrophic insider threats that go unnoticed by traditional SIEM solutions.
In an era when insider threats pose tremendous risk to organizations, User & Entity Behavior Analysis (UEBA) is, now more than ever, a must-have tool that helps organizations to timely detect and respond to intrusions before it is too late.
At a Glance
UEBA helps you save the day
The ClearSkies™ Cloud SIEM capitalizes on the User & Entity Behavior Analysis (UEBA) behavioral and predictive analytic capabilities, which are integrally complemented by ClearSkies™ Endpoint Detection & Response (EDR). The SIEM utilizes supervised and unsupervised Machine Learning (ML) and Artificial Intelligence (AI) modeling for continuous re-baselining of users’ and entities’ relationship behavior towards the effective detection of abnormal behavior. Deviations from any user’s normal behavior are analyzed to identify what caused this behavioral change, triggering an alert for further investigation before it is too late.
Behavioral Analysis Moods
Behavioral Analysis Moods indicate how the Agent categorizes activities into suspicious and/or malicious, and what “Actions” will be triggered for each. They are assigned to each user based on strategic organizational security objectives and risk appetite. The Behavioral Analysis are described below:
Simplify your reporting process
RELAXED | NEUTRAL | AGGRESSIVE |
Overview: This “Mood” adopts a lenient approach to the behavioral analysis for log and event data collected, where the “Actions” applied are for informative purposes only. Response actions: “Monitor and Alert” activities categorized as suspicious and/or malicious. | Overview: This “Mood” adopts a moderate approach to the behavioral analysis of the Agent for the log and event data collected, where the “Actions” applied are less restrictive. Response actions: “Monitor and Alert” activities categorized as suspicious, and “Alert, Block and/or Quarantine” activities categorized as malicious. | Overview: This “Mood” adopts a strict approach to the behavioral analysis of the Agent for the log and event data collected, where the “Actions” applied are restrictive. Response actions: “Alert and Block” activities categorized as suspicious, and “Alert, Block and/or Quarantine” activities categorized as malicious. |
UEBA helps you save the day towards the detection of suspicious and/or malicious activity, which would otherwise go unnoticed by traditional security defenses.
Demo request
See it in action!
Request a live demo from our representatives to experience the value of ClearSkies™.
